Background
Modern Windows systems include security mitigations like DEP, ASLR, CFG, and SafeSEH to help prevent memory-based attacks. The following sections describe methods to check whether these flags are enabled for an EXE or DLL.
Resolution
Solution 1: Static security flags check with Windows PowerShell
Download tool (GitHub): https://github.com/NetSPI/PESecurity and follow these steps to import the module in PowerShell:
1. Run: Get-ExecutionPolicy //Check execution policy
2. Review the return value: Restricted //Default state, no scripts allowed to run
3. Copy Get-PESecurity.psm1 to local directory
4. CD C:\Get-PESecurity //Navigate to directory
5. Run: import-module .\Get-PESecurity.psm1 //Import the module
Note:
Make sure the directory is not restricted. If access is denied, open PowerShell as Administrator.
If you see the message:
“cannot be loaded. The file C:\PESecurity\Get-PESecurity.psm1 is not digitally signed. You cannot run this script on the current system.”
Run the following command and enter "Y" when prompted:
set-ExecutionPolicy -ExecutionPolicy RemoteSigned
Check EXE flags by running this command
get-pesecurity -f C:\Users\Admin\Desktop\SQLpreview_mssql\testcase_sqlpreview.exe //This is the path of the EXE you want to inspect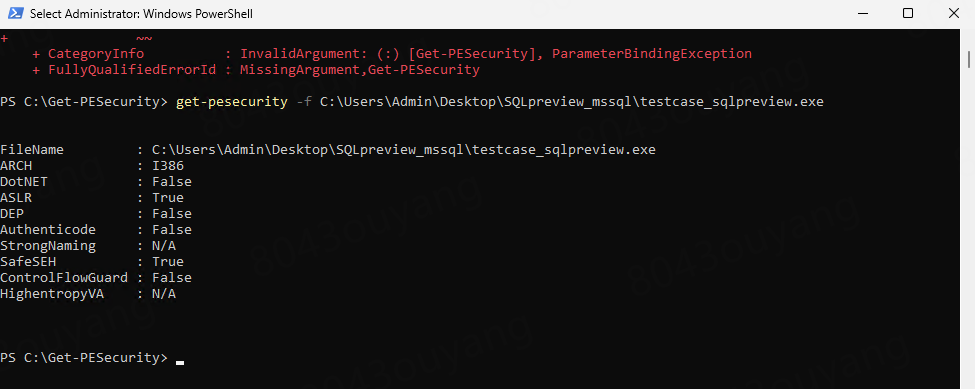
Check the returned True/False value to confirm whether the security flags are enabled.
Command to check security flags for all DLLs under the runtime directory
Get-PESecurity -directory "C:\Program Files (x86)\Appeon\Common\PowerBuilder\Runtime 25.0.0.3683" -recursive | Export-CSV csvfile.csv
Solution 2: Static security flags with DUMPBIN
Tool Installation
1. Visual Studio includes a Developer Command Prompt. Make sure you have installed the Desktop Development with C++ workload.
2. Alternatively, you can download and install the Lightweight Visual C++ Build Tools (with DUMPBIN) from this link: https://visualstudio.microsoft.com/visual-cpp-build-tools/ Check C++ build tools during installation
Check EXE flags
Run: dumpbin /loadconfig pb.exe //check security flags of EXE/DLL (common use)
1: enabled; 0: not enabled
Safe Exception Handlers: 1
CFG Guard: 1
NX Compatibility: 1
Dynamic Base: 1
"CFG Guard: Control Flow Guard"
"NX Compatibility: DEP (Data Execution Prevention)"
"Dynamic Base: ASLR (Address Space Layout Randomization)"
"Safe Exception Handlers: SafeSEH (Safe Exception Handling)"
dumpbin /HEADERS pb.exe //View file header (security flags, machine type, etc)
dumpbin /imports pb.exe //View dependent DLLs
dumpbin /? //View help and all available options
dumpbin /headers /loadconfig /imports C:\Users\appeon\AppData\Roaming\PBApps\Applications\172.16.9.79_salesdemo_cloud\salesdemo_cloud.exe > E:\Get-PESecurity\result.txt //Export to text file
Batch security flag check for DLLs
Example 1: Check security flags for all EXE/DLL in the current directory
for %i in (*.exe *.dll) do @echo ===%i ===&& dumpbin /loadconfig "%i" | findstr /i "CFG NX Dynamic Safe"
If enabled, the features will appear in the output. For example, Appeon.DB.Proxy.dll has ASLR, SafeSEH enabled.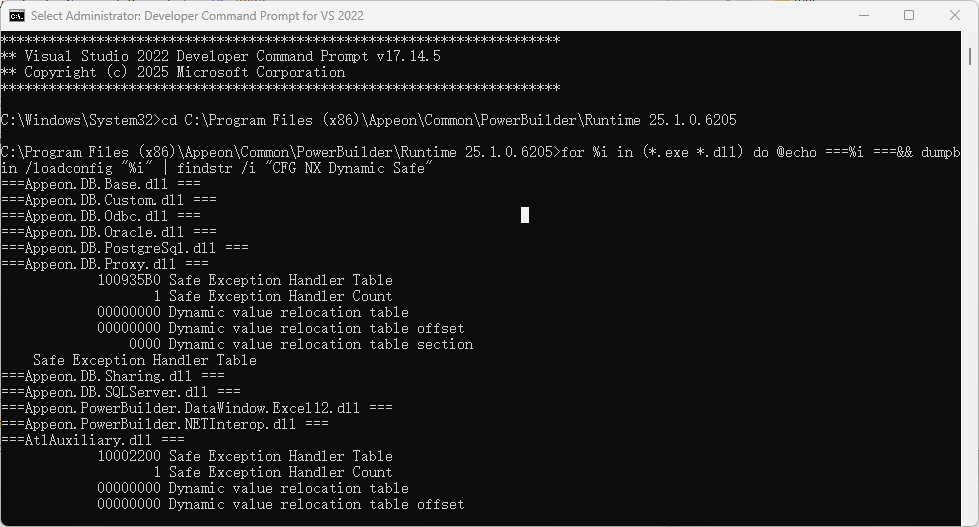
Example 2: Use a .bat script to check security flags for all EXE/DLL in the current directory
Place the attached check_security.bat into the target directory
Open Developer Command Prompt for VS 2022, navigate to .bat file and run.
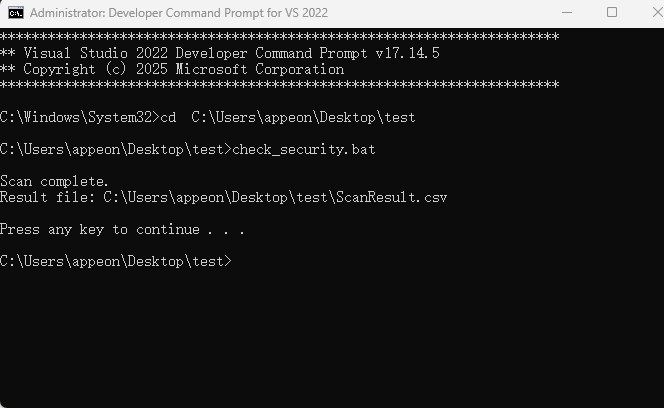
View output to confirm DLL security attributes.
Solution 3: Security Flags check with WinDbg
Using WinDbg to check the security flags of an EXE and its dependencies
Note: WinDbg is primarily a debugger for dynamic debugging, but it also supports static analysis
Download link: https://developer.microsoft.com/en-us/windows/downloads/windows-sdk
Attach to a running process
File -> attach to a process -> select a process you want to check //You can check a running process
After you attach to a process, it will list all loaded DLL module names and paths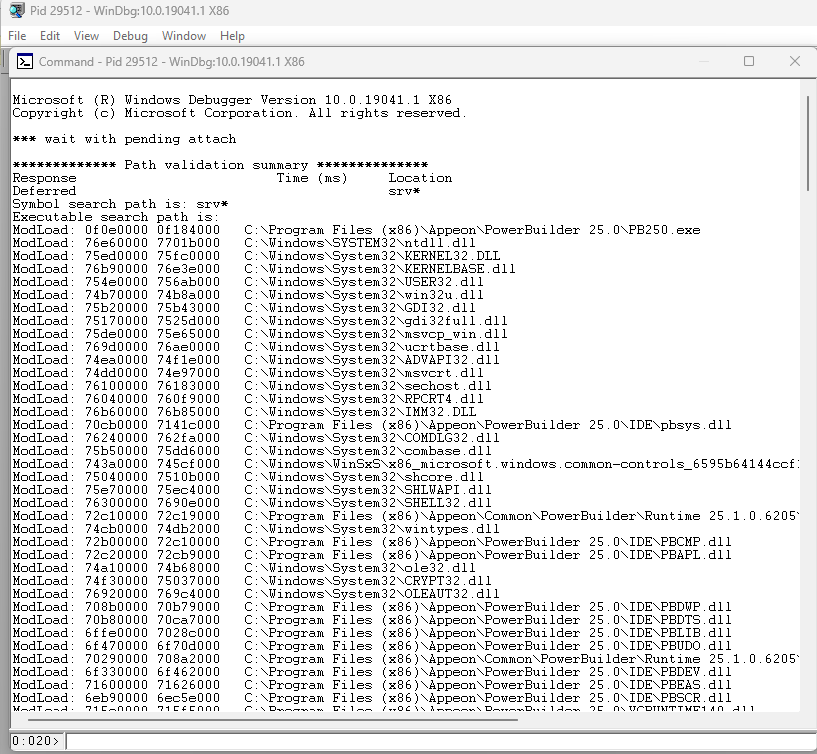
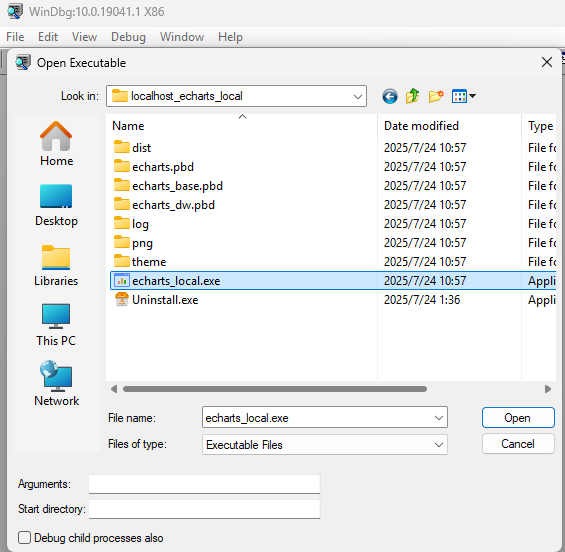
Open executable file
File -> Open Executable -> Go //Debugging a newly started program
After you choose an EXE, use Debug -> Go to start the program
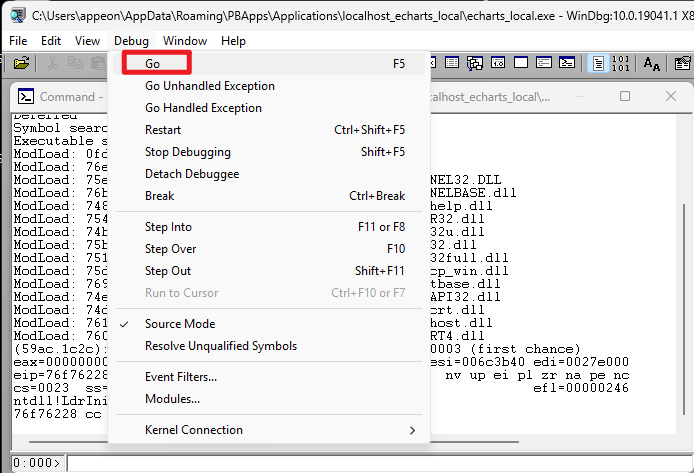
Note: For static analysis, you can skip “Go” and run commands directly in the command window.
Execute commands and check results
lm //List loaded modules (EXE itself + DLLs)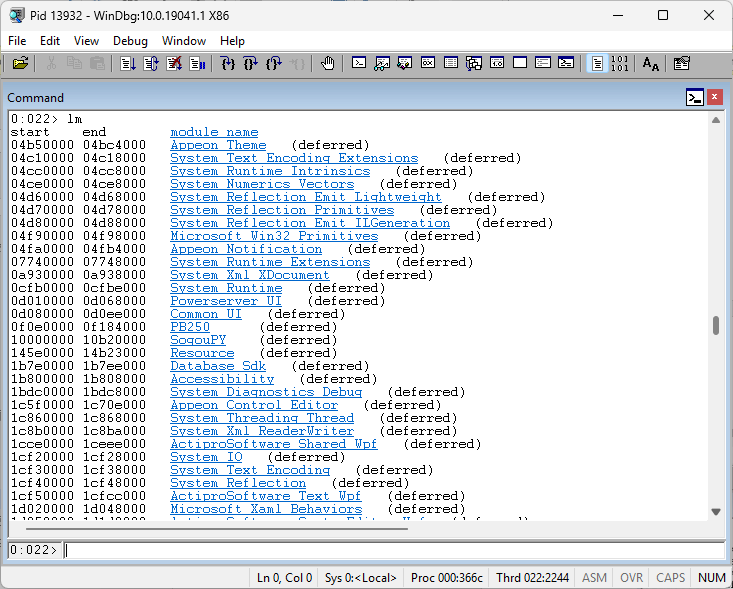
If you click on Appeon.Theme, you will see the detailed information (such as version, path, etc.)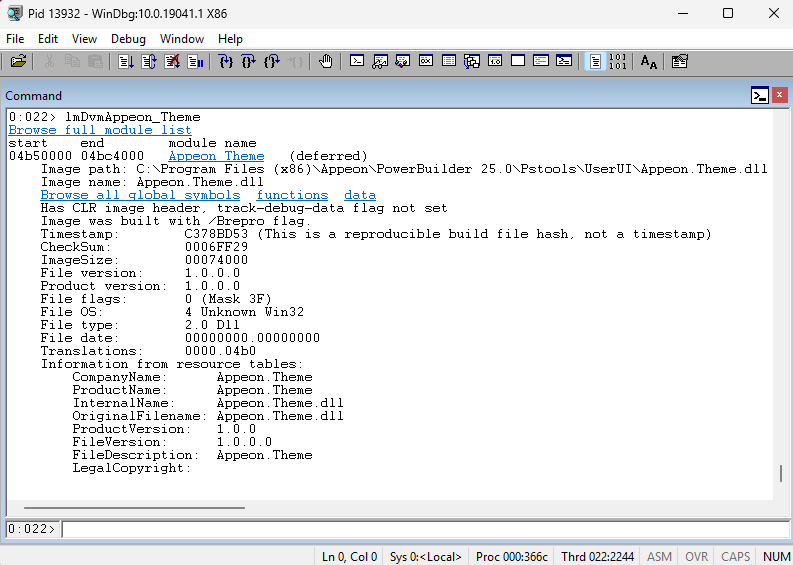
lmv //Detailed module info (version, Symbols, paths). You can check all DLL details from this exe. 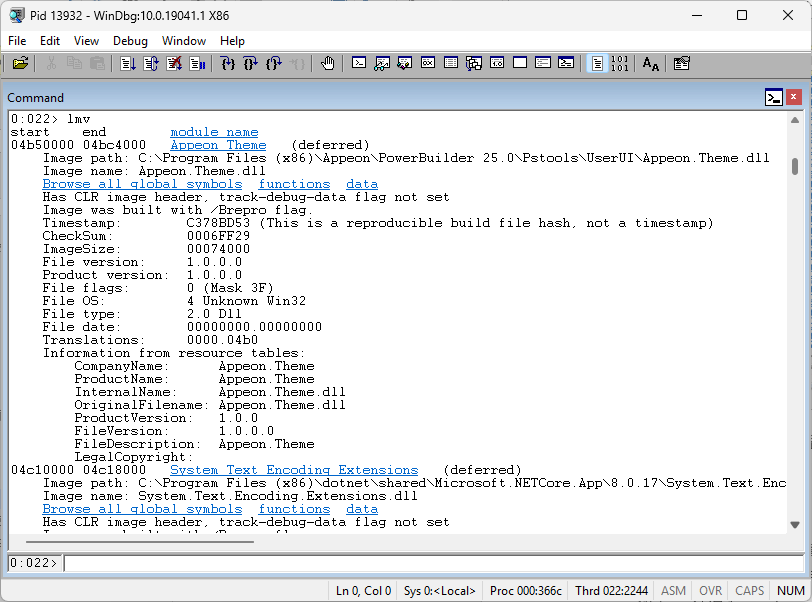
!dh [Module | Address | FilePath ] [Option] //Check DLL security attributes, for example: !dh 04b50000(Address)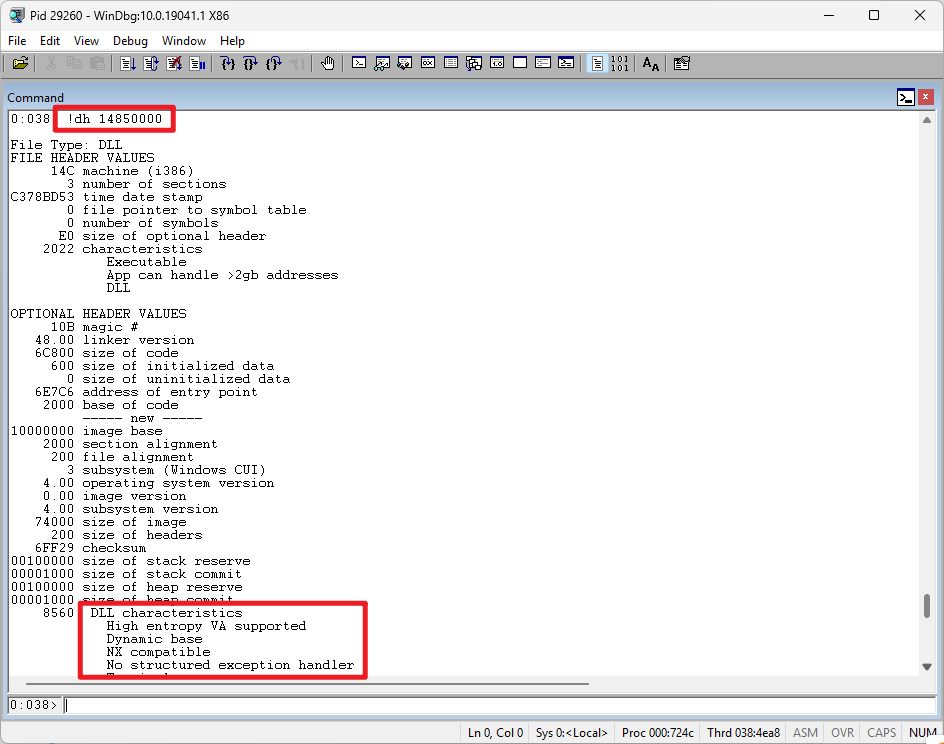
!dh -f //View PE Header info (security attributes)
.help //View basic usage of help command
How to Check DLL’s enabled security flags
Example 1: dynamic analysis of EXE/DLL security flags
As an example, let us check the security flags of appeon.theme.dll from PB250.exe
Attach to the running process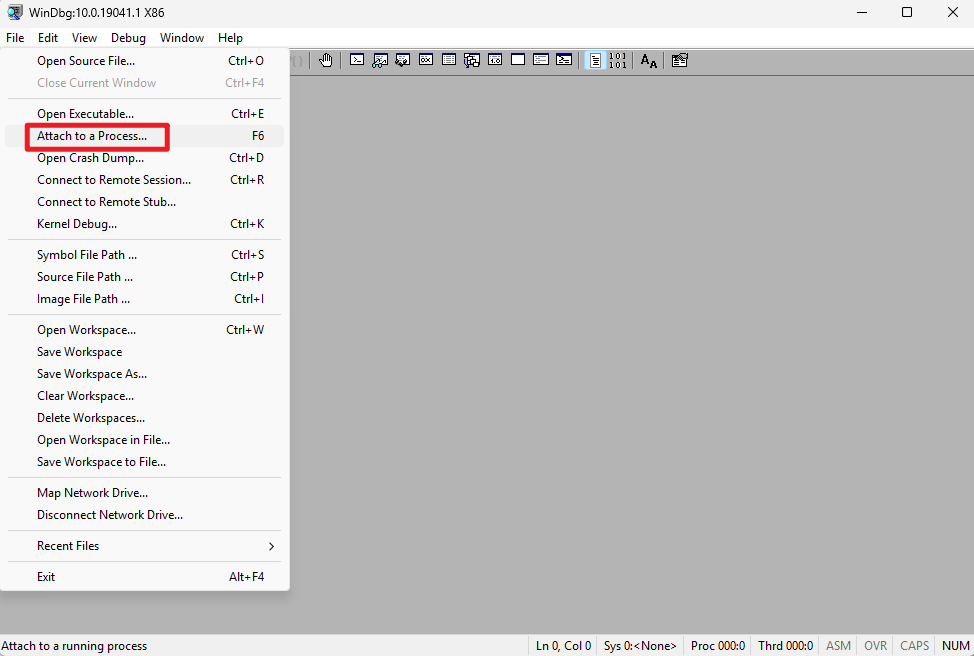
Only one target process can be attached for each debugging session.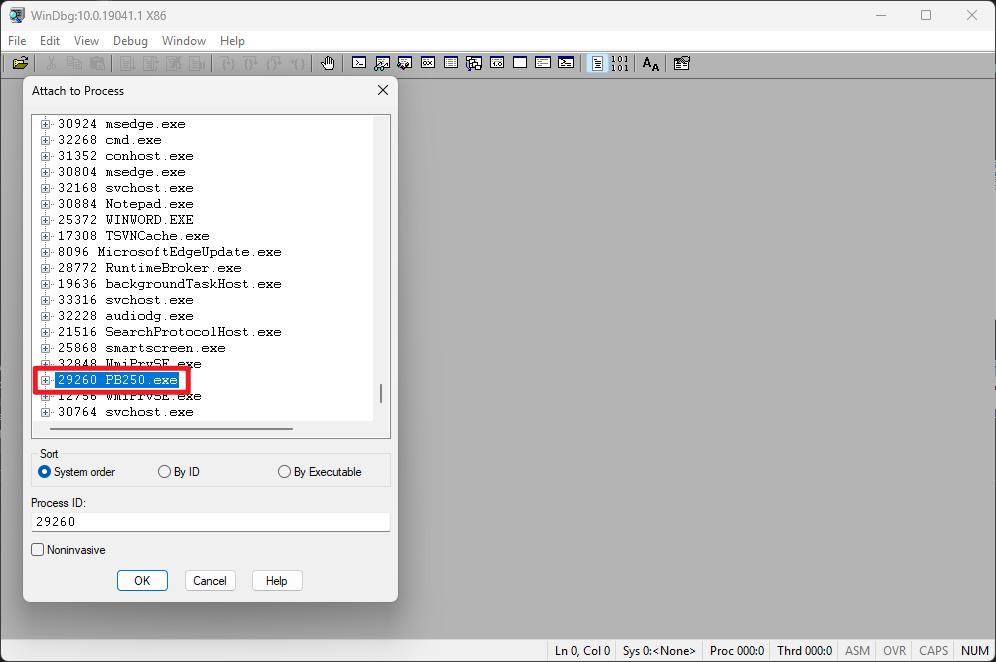
After you select the process, it will display the content of the loaded modules. You can also use lm command to get detail info of the modules.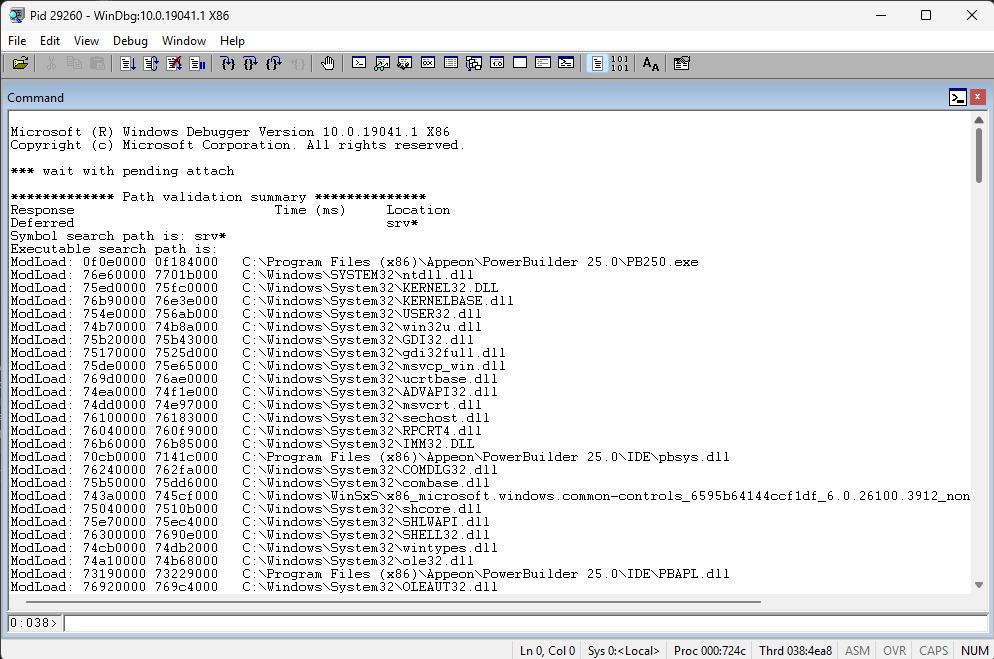
You can use Ctrl+F to find the module info are looking for if there are too many data in the output.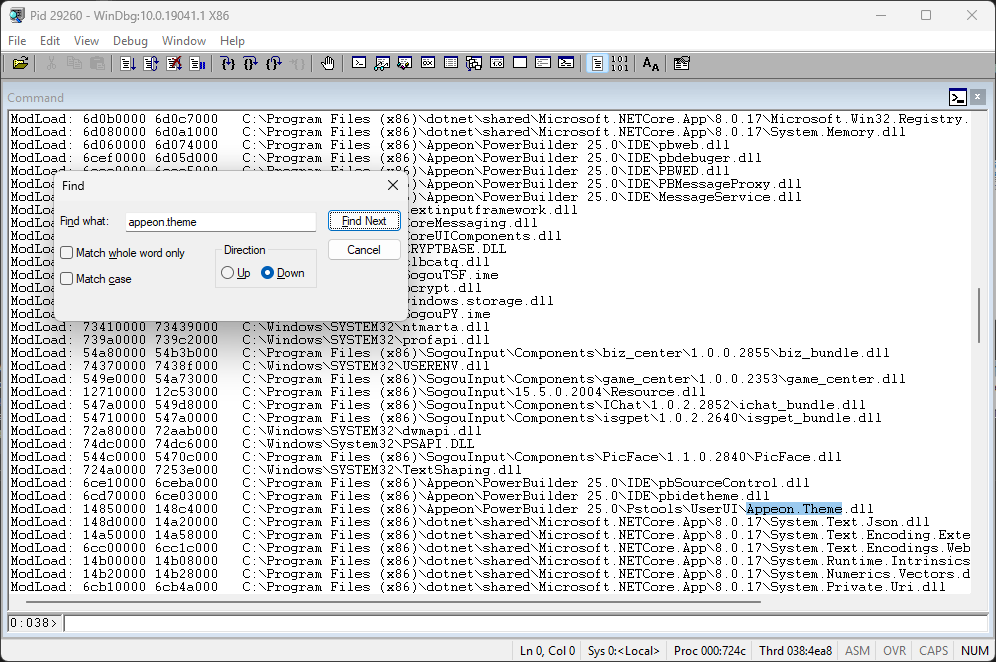
Based on the module information obtained, enter the command !dh 14850000 to check the security attributes of Appeon.Theme.dll (The current argument the address)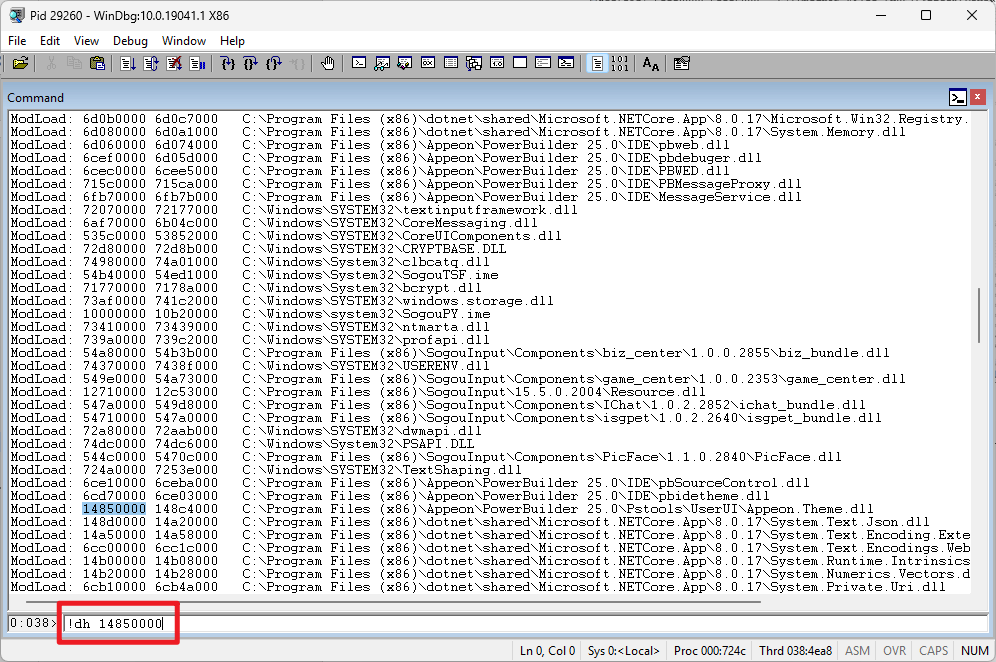
Check the output. You can use Ctrl+F to find DLL characteristics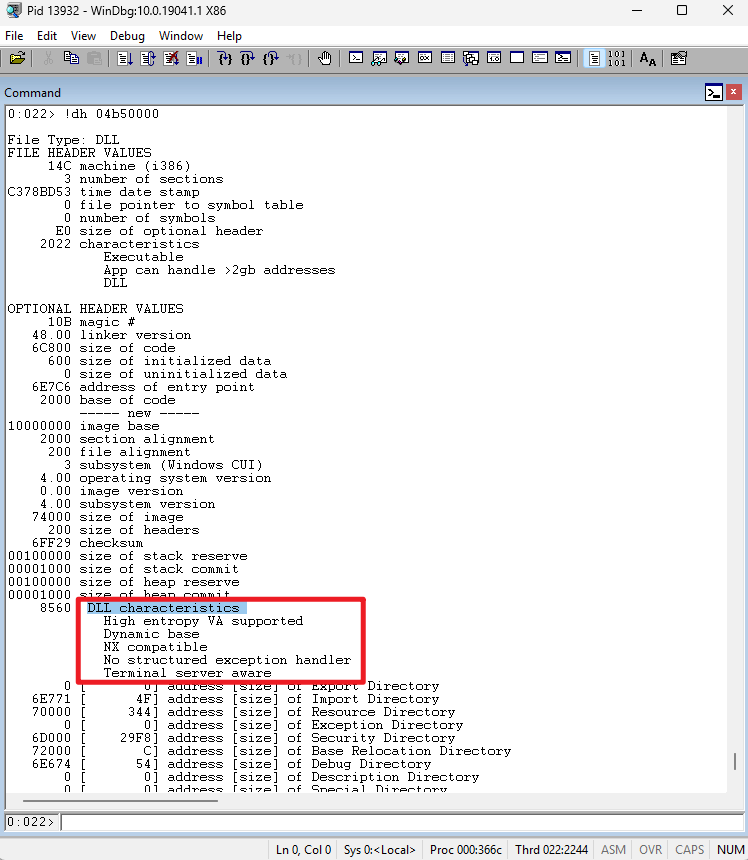
Based on the DLL characteristics obtained, you can confirm that this DLL has ASLR and DEP enabled. You can refer to the following reference:
Dynamic Base: Supports ASLR
NX Compatible: Enables DEP
Guard CF: Enables CFG
SafeSEH / No SEH: Related to SEH security
Note: After you attach to a process, closing WinDbg will terminate the process too. You can choose ”Debug->Detach Debuggee” or run .detach in the command to avoid terminating the process.
Example 2: Static analysis of security flags of EXE/DLL
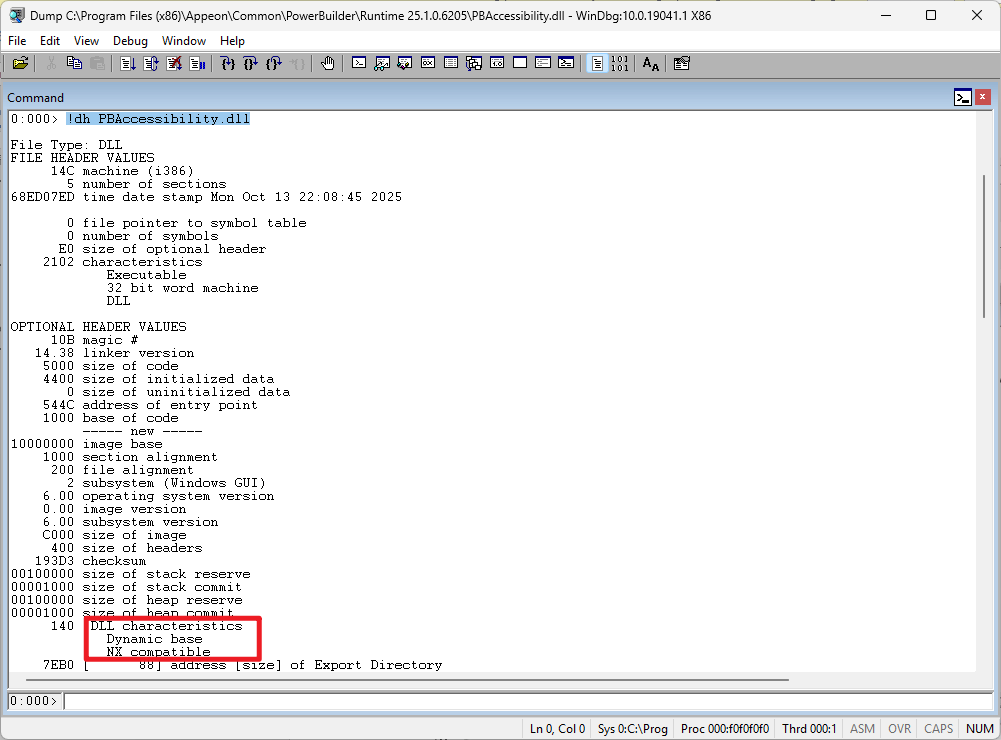
Check the security flags of a single file PBAccessibility.dll
Choose Open Crash Dump… Do not use Open Executable as it will throw an error (You can only start a executable file (exe). Use this method when you want to do static analysis of a DLL loaded by an exe)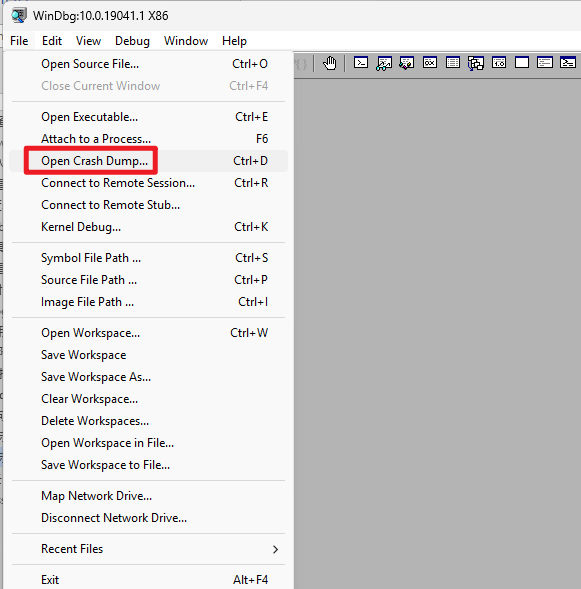
Choose the DLL file you want to analyze. You can only see exe and dll files when you choose ALL Files.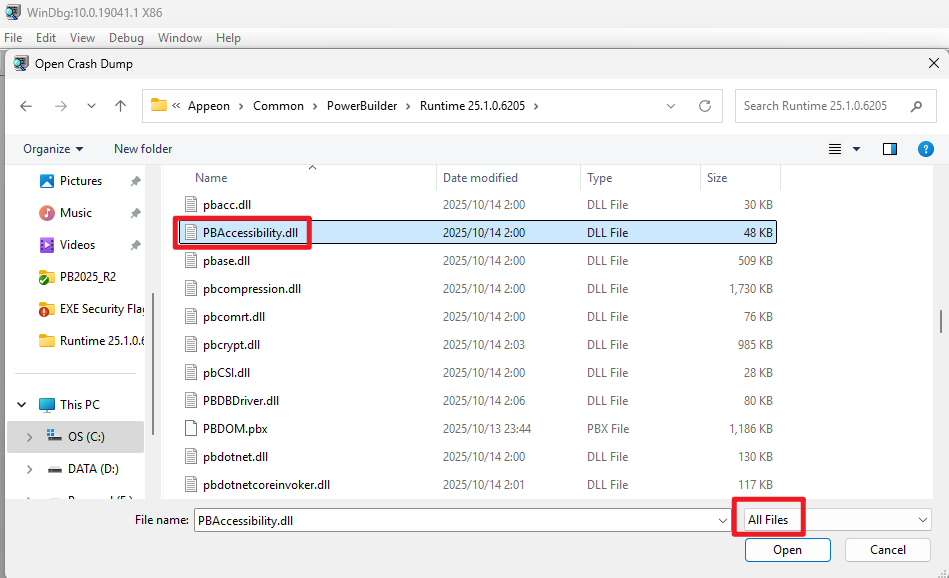
Use command: !dh PBAccessibility.dll to check the security flags of this DLL.